Is the "blind spot" DNS of information security measures protected?-Municipal communication online
Initiatives of private companies
Cyber-attack countermeasures
Infoblox Co., Ltd. Solution Technology Headquarters (Japan/Korea) General Manager Toru Takahashi Sales Department Account Manager (Public/Education) Hiroki Tsuchiya [Provided] Infoblox Co., Ltd. January 2010 issue), the article is from the time of the interview.Local governments that handle residents' personal information are required to continuously strengthen information security measures. Against this backdrop, Mr. Takahashi of Infoblox, a vendor specializing in DNS servers, points out that "many local governments have insufficient countermeasures against cyberattacks that exploit DNS*1." In recent years, what kind of countermeasures should be taken against the threat that the damage is increasing rapidly? Mr. Tsuchiya of the company also asked about the details.
Click here for the service overview document introduced in this article Infoblox Co., Ltd. Solution Technology Headquarters (Japan/Korea) General Manager Toru Takahashi Infoblox Co., Ltd. Sales Department Account Manager (Public/Education) Hiroki Tsuchiya Hiroki Tsuchiya―What are the current concerns about information security measures taken by local governments?
Tsuchiya: The number of cyberattacks that exploit DNS is increasing. DNS is a basic network protocol that converts between domain names such as "△△.com" and IP addresses. For example, when browsing a website, our computer queries the DNS server for the IP address corresponding to the domain name, and the DNS server finds that IP address and responds to the computer. Then, DNS communication*2 is performed such that the computer accesses the website with that IP address. By exploiting this mechanism to send malware to personal computers or perform remote control, cyberattacks to extract confidential information of users and organizations are increasing rapidly.
- How is the situation of countermeasures?
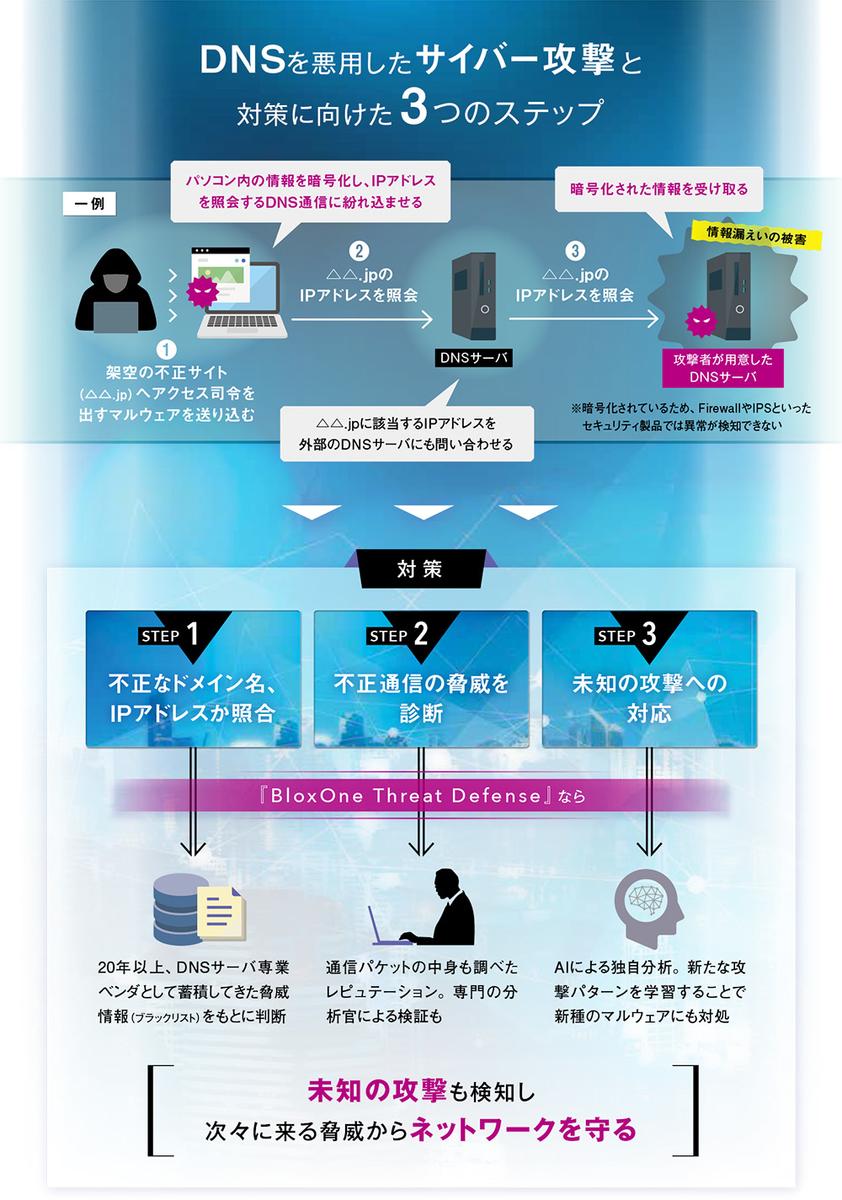
Takahashi: According to our survey, nearly 70% of companies and organizations, including local governments, have yet to take measures. There are two main reasons for this. One is the fact that DNS communication, which underpins the foundation of Internet communication, has been trusted as 100% safe. Therefore, most companies do not even acquire DNS communication logs themselves. The second is a lack of awareness of cyberattacks on DNS. In recent years, cyberattacks are becoming more sophisticated, and defense nets are easily breached. Currently, we believe that security measures for DNS, which can be said to be a "blind spot", are urgently needed.
Tsuchiya: However, there are difficulties. Even if an attack is detected, the DNS server cannot be blocked easily. This is because if the DNS server is blocked, various applications that connect to the Internet will not be available, which will have a significant impact on the entire business.
- What should I do?
Tsuchiya: It is necessary to build a defense system that specializes in DNS. For example, we have developed a security system called "BloxOne Threat Defense" by combining the knowledge we have accumulated over 20 years as a vendor specializing in DNS servers.
- What kind of system?
Takahashi First, when we detect a suspicious domain name or IP address, we accurately determine whether the domain name or IP address has evidence of abuse based on the vast amount of threat information we possess. . At that time, in addition to verification by a specialized analyst, the contents of those communication packets are also examined to diagnose the threat level. In many cases, it is possible to determine the presence or absence of threats at this point, but since unknown attacks are also increasing rapidly, we are also conducting real-time analysis using AI. This is a patented technology of our company, and AI that specializes in detecting DNS communication behavior analyzes and judges the threat level on a daily basis, learns new attack patterns in real time, and is a function that can deal with new types of malware. .
Tsuchiya: In the unlikely event that an attack is detected, there is a function to identify which DNS communication was sent through which device, and that communication can be blocked to minimize the impact on business.
- Do you have a track record of implementation?
Tsuchiya: It has already been introduced by multiple public institutions. I hope many local governments that are trying to strengthen information security will use it.
Toru Takahashi Profile Toru Takahashi has worked in the IT and security industries for over 20 years and has held various technical positions. He joined Infoblox Co., Ltd. in 2016 and engaged in proposal activities and enlightenment activities as a solution architect. Incumbent since 2018. Hiroki Tsuchiya Profile Joined Infoblox Co., Ltd. in 2020 after engaging in sales operations for public institutions for about 8 years. Mainly in charge of sales operations for the public and educational markets. Incumbent since 2021. Infoblox Inc.| Establishment | September 2004 |
|---|---|
| Capital | 10 million yen |
| Number of employees | 18 (as of October 2021) |
| Building information security infrastructure | |
| URL | https://www.infoblox.co.jp/ |
| Contact phone number | Sales Department 03-5772-7211 (Weekdays 9:00-18:00) |
| Contact email address | SalesJapan@infoblox.com |
*1: *DNS: Abbreviation for Domain Name System. A system on the Internet that associates and manages domain names and IP addresses
*2: *DNS communication: Communication that follows the mechanism of DNS
 notebook-laptop
notebook-laptop