Analyzing New Ransomware "BlackMatter"
BlackMatter is a new ransomware threat discovered at the end of July 2021.
This malware was recognized by powerful attack groups and advertisements from developers who allegedly used parts of other malware such as GandCrab, LockBit, and DarkSide. Also called a group. Analyzed by McAfee Enterprise Advanced Threat Research (ATR), this malware has much in common with DarkSide, the malware associated with attacks on the colonial pipeline that attracted the attention of the U.S. government and law enforcement agencies around the world. It turns out there is.
The main purpose of BlackMatter is to encrypt files on infected computers and demand a ransom to decrypt them. As with previous ransomware, operators steal files and personal information from compromised servers, threaten to publish them on the internet, and demand an additional ransom.
Coverage and Protection Advice
McAfee's EPP solution covers BlackMatter ransomware with a suite of prevention and detection techniques.
ENS ATP provides behavioral content focused on proactively detecting threats, while also providing known IoCs for both online and offline detection. For DAT-based detection, the family is Ransom-BlackMatter! is reported as ENS ATP achieves a 2 Adds an extra layer of protection.
Indicator updates are pushed through GTI, and Insights customers find a threat profile for this ransomware family. This profile will be updated when new relevant information becomes available.
Technical Details
BlackMatter is usually considered an EXE program, and in special cases a DLL (dynamic library) for Windows. Linux machines can also be affected by special versions of it, but this report will only cover Windows versions.
In this report, we will focus on version 1.2 of BlackMatter, while also noting important changes in the current version 2.0.
BlackMatter is programmed in C++ and is 67Kb in size.
Figure 1: Information about malware
The compile date of this sample is July 23, 2021. These dates can be changed, but I believe they are correct. The compile time for version 1.9 is August 12, 2021, and the latest version, 2.0, is dated four days later, August 16, 2021. It's clear that malware developers are actively improving their code to make it harder to detect and analyze.
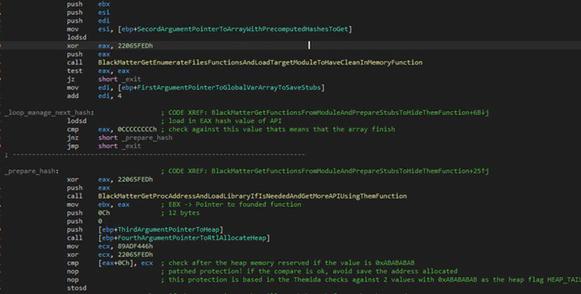
The first action performed by BlackMatter is the preparation of some modules that will be required later to obtain the required functionality of Windows.
Figure 2: BlackMatter searching for functions
BlackMatter uses several tricks to make analysis difficult and to avoid debuggers. Instead of looking up the module name, it checks a pre-computed hash with the ROT13 algorithm. The required modules are "kernel32.dll" and "ntdll.dll". Both modules try to get a function to reserve memory in the process heap. The API is searched using a combination of the module's PEB (process environment block) and EAT (export table address) to enumerate all function names. These names are used to compute a custom hash and match it against the target hash.
Figure 3: BlackMatter detecting debuggers
At this point, BlackMatter will create a special code to detect the debugger and will check the last two "DWORDS" after the memory is reserved to search for the byte "0xABABABAB". These bytes are always present when a process reserves memory in the heap, and if the heap has one special flag (which is set by default when the process is in the debugger), the malware Avoid storing pointers to memory that has In this case the variable holds a null pointer.
In the Windows operating system, the state of memory differs depending on whether the program is running in normal mode (as usual) or in debug mode (such as the mode used by programmers). In this case, when memory is reserved to hold information, Windows marks the end of this memory with a special value "0xABABABAB" when in debug mode. BlackMatter will check this value and detect the debugger if found. To prevent successful execution, discard the previously obtained function address. In other words, it crashes and avoids execution.
Figure 4: Preparing protection stub function
After this check, a special stub is created in the reserved memory. This is very simple, but effective in making analysis difficult as it requires stubbing to see which functions are called and executed.
This procedure will be executed using all the required functions. The hash is stored hard-coded in the middle of the ".text" section of a small struct as data. The end of each structure is recognized by checking against the "0xCCCCCCCC" value.
Figure 5: Hash of required features
This behavior highlights that BlackMatter developers know some tricks to make analysis difficult, but it's easy to disable both by patching the binary is.
After this, the ransomware uses another trick to avoid using the debugger. BlackMatter calls the function "ZwSetInformationThread" with a class argument of 0x11. This hides the calling thread from the debugger.
If the malware does it correctly and the debugger is connected, the debugging session will end immediately. This code will later run in the thread used to encrypt the file.
Figure 6: Another way to detect the debugger
The next action is to use the function "SHTestTokenMembership" to check whether the user who started the process belongs to the local group of administrators on the machine. If the user is in the Administrators group, the code continues as normal, otherwise it uses PEB to get the operating system version (for API functions that may change the version). to avoid using it), open the process if available and check the token to see if it belongs to the Administrators group.
Figure 7: BlackMatter checking for admin privileges
The process token uses a neat trick to elevate privileges if the user does not belong to the administrator group.
The first action is to prepare the string "dllhost.exe" and enumerate all loaded modules. For each module, it checks one field in the initial structure that all executables have, holds the base memory address where it is loaded (eg kernel32.dll at 0x7fff0000), and compares it to its own base address. If they are equal, change the name of the PEB field and the path and arguments path to "dllhost.exe" (for the path and arguments path to the SYSTEM32 folder where the canonical "dllhost.exe" resides). This trick is used to mislead users. For each module found, it checks the module's base address with its own base address, at which point it changes the loaded module's name, path, and arguments to mislead the user.
Figure 8: Decryption of string "dllhost.exe"
The process name will be "dllhost.exe" and the path will be the system directory of the victim's machine. This trick, in addition to not renaming the process in the TaskManager, can make the debugger "think" that another binary is loaded, removing all breakpoints (depending on which debugger you use increase).
Figure 9: Change PEB name and path
The second action uses a single exploit using a COM (Component Object Model) object to elevate privileges before terminating its own instance using the "Terminate Process" function. is to try.
For detection, the module uses the undocumented function "LoadedModulesLdrCallback" of NTDLL.DLL. This allows the programmer to set the function as a callback, get the arguments and check the PEB. In this callback, the malware uses 'RtlInitUnicodeString' to set a new Unicode string. The string is the path to "dllhost.exe" in the system folder and "dllhost.exe" as the image name.
The exploit used to bypass public UAC (User Access Control) uses CMSTPLUA's COM interface and COM ElevationMoniker.
If you have administrator privileges or successfully used an exploit, we will continue to create new extensions to be used with encrypted files. This task reads the registry key for "MachineGuid" in the encryption key (HKEY LOCAL MACHINE).
This entry and value exists in all versions of Windows and is machine-specific. Use this value to create a custom hash to get the final 9-character string.
Fig 10: Creation of new extension for encrypted files
The malware then creates a name for the ransom note and calculates its integrity hash. The ransom note text is stored encrypted in the malware data. The ransom note is usually named “%s.README.txt” with the wildcard populated with the new extension previously generated.
The next step is to acquire the privileges that will be needed later. BlackMatter tries to get many privileges.
・SE_BACKUP_PRIVILEGE・SE_DEBUG_PRIVILEGE、SE_IMPERSONATE_PRIVILEGE・SE_INC_BASE_PRIORITY_PRIVILEGE・IF_INCREASE_QUOTA_PRIVILEGE・SE_INC_WORKING_SET_PRIVILEGE・SE_MANAGE_VOLUME_PRIVILEGE・SE_PROF_SINGLE_PROCESS_PRIVILEGE・SE_RESTORE_PRIVILEGE・SE_SECURITY_PRIVILEGE・SE_SYSTEM_PROFILE_PRIVILEGE・SE_TAKE_OWNERSHIP_PRIVILEGE・SE_SHUTDOWN_PRIVILEGE
Figure 11: Special Privilege Settings
After obtaining permissions, check if you have SYSTEM permissions and check the token of your own process. For SYSTEM, use the function "WTSQueryUserToken" to get the right user to logon. This function can only be used if the caller has "SeTcbPrivilege" which only SYSTEM has by default.
Figure 12: Obtaining a token for the logged-on user
After obtaining the logged-on user's token, the malware opens a Windows station and desktop.
If you don't have SYSTEM privileges, it will enumerate all processes in the system and try to clone the token from "explorer.exe" (the name is checked using a hardcoded hash). If so, it will continue as normal. Otherwise check again if the cloned token has admin privileges.
In this case, it will continue as usual, but otherwise the operating system version and CPU (Central Processing Unit) mode (32-bit or 64-bit) will be checked. This check is performed using the function "ZwQueryInformationProcess" of class 0x1A (ProcessWow64Information).
Figure 13: Check if your operating system is 32-bit or 64-bit
If the system is 32-bit, decrypt one small shellcode inserted into one process enumerated using the normal "CreateRemoteThread" function. This shellcode is used to obtain process tokens and elevate privileges.
If your system is 64-bit, decrypt two different shellcodes, execute the first shellcode, and get the second shellcode as an argument.
Figure 14: Mutex creation to avoid multiple instances
These shellcodes allow BlackMatter to elevate privileges in a clean way. To get the SYSTEM token, BlackMatter not only enumerates the processes and gets "svchost.exe", it checks the name of the process, but also checks that the process has the privilege "SeTcbPrivilege" It is important to understand that Since by default only SYSTEM has it (and it's one permission that can't be removed from this "user"), this process is running under SYSTEM, so attack it with a shellcode and steal the token be the perfect target for Duplicated and set to BlackMatter.
Figure 15: Checking if the target process is SYSTEM
After this, the configuration embedded in one section will be decrypted. BlackMatter has this configuration base64 encrypted and encoded.
This configuration has a very similar structure to Darkside, and provides another clear hint that the developers are the same, despite claims to the contrary.
After decryption, the configuration can obtain the following information.
- RSA key used to protect Salsa20 key used to encrypt files - 16-byte hex value indicating victim ID - Used to encrypt information sent to C2 A 16-byte hex value that is the AES key to be used An 8/9-byte array with behavior flags to control the behavior of the ransomware A DWORD that holds the value to reach the key points in the configuration Special arrays (4-byte values each) Various blocks are encoded and sometimes re-encrypted to further protect the field
After retrieving and parsing the configuration, BlackMatter will start checking if the user in the configuration needs to be logged in. In this case, use the function "LogonUser" with the user's information held in the configuration. This information has one user and one password. "test@enterprise.com:12345". 'test' is the user, '@enterprise.com' is the domain, and '12345' is the password.
The next action is to check the flag to see if a mutex should be created to prevent multiple instances from occurring.
This mutex is unique for each machine and is based on the registry entry "MachineGuid" under the key "Cryptography". If the system already has this mutex, the malware will automatically terminate.
Using a mutex to create a vaccine can be useful, but not in this case as the developer can change the algorithm and avoid creation by simply setting the flag to false.
Figure 16: Mutex creation to avoid multiple instances
Afterwards, check whether information needs to be sent to the C2. If infected (usually, but not always), get information about the victim's machine, such as username, computer name, hard disk size, and other information that helps malware developers know how many machines have been infected To do.
This information is base64 encoded and encrypted with AES using the configuration key.
Figure 17: Encrypted information sent to C2
The C2 address is included in the configuration (but not all samples have a C2 address. In this case, the send flag is false). The malware will attempt to connect to the C2 using normal protocols, or use SSL to check for "http" at the beginning of the string.
Figure 18: Retrieve victim's machine and user information
Information is prepared with several strings decrypted from the malware and sent in a POST message.
Figure 19: Choose to send via HTTP or HTTPS
This message has a value that misleads the check and hides the true information as garbage. This "fake" data is calculated randomly.
C2 returns garbage data, but the malware checks whether it starts and ends with the characters "{" and "}". In that case, the malware ignores sending information to another C2.
Figure 20: Confirmation of response from C2 after sending
BlackMatter is a multi-threaded application, and the procedure for sending data to C2 is executed by a secondary thread.
After that, BlackMatter will enumerate all units that can be modified and deleted to destroy the contents of the Recycle Bin. The malware creates it for each unit it has and is of the correct type. One difference with DarkSide is that there is a flag for this behavior while BlackMatter does not.
The next action is to delete the shadow volume using COM to avoid detection using normal programs that manage shadow volumes. This differs from DarkSide which has a flag for this purpose.
Figure 21: Shadow volume destruction using COM
BlackMatter checks another flag, enumerates all services based on one list in the configuration, stops and removes the target service.
This behavior is the same as DarkSide.
Figure 22: Stopping and deleting services
Processes are checked and terminated in the same way as DarkSide based on other configuration flags.
After terminating the process, BlackMatter will prevent threads from being suspended or hibernated if someone is using the computer and one of these consequences occurs during file encryption to prevent This is done using the function "ZwSetThreadExecutionState".
Figure 23: Prevent machine from suspending or hibernating
The next action is to create a thread to enumerate all fixed and network units and encrypt the files. BlackMatter uses Salsa20 to encrypt part of the file and save a new block at the end of the file. This block is protected with an RSA key embedded in the configuration using the Salsa20 key used for encryption. This makes BlackMatter slower than many other ransomware.
After encryption, all information about the encryption process, the number of encrypted files, the number of failed files, etc. will be sent to the C2. This information is sent in the manner described above, but only if the configuration is set to true.
Figure 24: Release mutex
If a mutex is created at this moment, it will be released. Later we will see how the machine boots using the function "GetSystemMetrics". If booted in safe mode, BlackMatter will set some keys in the registry to make it persistent for the next reboot, attack the system and change the desktop wallpaper.
Figure 25: Determining whether the system will boot into safe mode or normal mode
Then disable the safe boot option on the machine and reboot (this is one of the reasons why shutdown privileges are required).
The permanent key value containing the malware path starts with "*" to enable booting in safe mode.
Figure 26: Setting Persistence Registry Keys
When the machine boots normally, a run-time generated alternative will change the desktop wallpaper and display text about the ransom note.
Figure 27: BlackMatter creates a new wallpaper at runtime
Versions 1.9 and 2.0
The new version has some differences compared to versions 1.2 to 1.6.
・Change of stub generation code. Previously, only one type of stub was used, but in recent versions, multiple types of stubs are used, with one randomly selected for each function. And you can remove the stub without any problem by patching the binary. A new byte flag in the configuration that indicates whether the ransom note should be printed using any printer available on the system. Very similar to Ryuk, but instead BlackMatter uses the "winspool.drv" API.・Remove one C2 domain that was shut down by the provider
Additional changes in version 2.0:
・This version changes the encryption algorithm to protect the configuration and makes decryption more complex ・Remove the last C2 shut down by the provider ・Add a new C2 domain
These changes suggest that developers are actively working on social media out of concern for malware and security researchers.
Vaccine
Unlike some ransomware we've seen in the past, such as GandCrab, BlackMatter has good code, but it can be used to avoid malware encrypting your files. It has some design flaws.
This vaccine is not intended to be used in a normal way, and is intended to be used only in special cases, as other programs may be affected while it is functioning. (Obviously we can't test every third-party program, but potential problems could include data corruption or unpredictable behavior), and the fix is not permanent.
Steps to make a vaccine (Proceed at your own risk):
Open regedit (or another registry editor) and navigate to the HKEY_LOCAL_MACHINE>Cryptography key. This key will display a string value named "MachineGuid" with a special value. This value is machine-specific and is used by some applications to identify the machine. BlackMatter uses this to create a mutex and, very importantly, a new extension for encrypted files.・Create a new value of string type with a random name and enter the same value as displayed in "MachineGuid" to back it up. Delete the "MachineGuid" value, then create it again, but using the binary type of the same name "MachineGuid" instead of the string type. • Close the Registry Editor.
Currently, BlackMatter cannot affect the machine as it needs a registry key to extend the ransom. Most importantly, if BlackMatter cannot create one, return the function without decrypting the required configuration. In this case it would discard the Recycle Bin and Shadow Volume anyway, but would exit later because there is nothing to do, an RSA key to protect the files, or anything to send to the C2 because the flags weren't read from the config. increase. (and the default values are all false).
While the behavior of other programs may be unpredictable, a vaccine can easily be created and the system will boot. This shows that the BlackMatter programmers made a mistake in designing their code.
This vaccine works on all versions, including 2.0.
MITER ATT&CK
This sample uses the following MITER ATT&CK™ technique.
| Technique ID | Technique description | Summary |
| T1134 | Manipulating Access Tokens | BlackMatter accesses and manipulates various process tokens. |
| T1486 | Data encrypted to impact | BlackMatter uses a custom Salsa20 algorithm and RSA to encrypt the file. |
| T1083 | Find Files and Directories | BlackMatter uses native functions to find targets to encrypt Enumerate files and directories. |
| T122.001 | Changing Windows File and Directory Permissions | BlackMatter uses the command icacls “ |
| T1562.001 | Disable or modify tools | BlackMatter has stopped services related to endpoint security software To do. |
| T1106 | Native API | BlackMatter uses native API functions in all its code. |
| T1057 | Process Discovery | BlackMatter enumerates all processes and attempts to detect and terminate security programs increase. |
| T1489 | Stop Service | BlackMatter will stop service. |
| T1497.001 | System Check | BlackMatter will check the memory reserved in the heap and start the debugger. try to detect. |
| T1135 | Discovering Network Shares | BlackMatter uses the following format for each driver letter from A to Z: Attempt to detect network shares by building a UNC path with \\ |
| T1082 | Find System Information | BlackMatter uses functions to Get information about |
| T1592 | Gathering victim host information | BlackMatter captures information about users and machines. |
| T1070 | Valid account | BlackMatter uses a valid account to log onto the victim's network . |
| T1547 | Boot or Logon Autostart Execution | BlackMatter installs persistence in the registry. |
| T1102 | Query Registry | BlackMatter queries the registry for information. |
| T1018 | Remote System Discovery | BlackMatter enumerates remote machines in a domain. |
| T1112 | Modify Registry | BlackMatter modifies registry keys and values and sets new ones. |
Conclusion
BlackMatter is a new threat in the ransomware field, and its developers use it to attack their targets I fully understand how to do it. The coding style is very similar to DarkSide and in our opinion the people behind it are either the same or very closely related.
BlackMatter shares many ideas with DarkSide and shares code to some extent.
· The configuration is very similar to the last version of Darkside, especially, but the algorithm to protect it has changed, it has fewer options, but it remains the same structure. The BlackMatter developers don't believe they achieved this similarity by reversing DarkSide. Because that level of coding skill allowed me to create an entirely new ransomware from scratch. Also, the idea that DarkSide's developers contributed or sold the original code is moot since it's an older product. • Dynamic functions are used in a similar fashion to DarkSide. • Use the same compression algorithm for configuration. - Victim IDs are retained in the same way as DarkSide.
Keep your McAfee Enterprise products up-to-date, avoid insecure remote desktop connections, maintain secure passwords that change regularly, take precautions against phishing emails, and keep unwanted devices out of your enterprise network. It is important not to connect to
Despite some effective coding, there was a mistake made by the developer, who was able to read the program and create a vaccine, but it could affect other programs and cause permanent damage. We reiterate that it is not a permanent solution and should only be used if the risks involved are acceptable.
*The content of this page is the content of the following McAfee Enterprise Blog updated on September 22, 2021 (US time). Original: BlackMatter Ransomware Analysis; The Dark Side Returns Author: Alexandre Mundo and Marc Elias
■ Related sites
 notebook-laptop
notebook-laptop